IPsec Direct Encapsulation – WAN for the Enterprise
2 min read
IPsec’s tunnel mode enables it to be used as a standalone connection method; this is the most fundamental VPN design model. When you are using IPsec direct encapsulation, dynamic routing protocols and IP multicast are not supported. The headend IPsec terminating device needs to use static IP addressing, but the remote IPsec endpoints can use static or dynamic IP addressing. Redundancy can be provided at the headend by using multiple IPsec terminating devices, and each remote IPsec endpoint can be populated with a list of headend endpoints to make connections with.
IPsec packet payloads can be encrypted, and IPsec receivers can authenticate packet origins. Internet Key Exchange (IKE) and Public Key Infrastructure (PKI) can also be used with IPsec. IKE is the protocol used to set up a security association (SA) with IPsec. PKI is an arrangement that provides for third-party verification of identities.
Figure 8-10 shows the topology for IPsec direct encapsulation with multiple headend sites to provide resiliency for the branch offices.
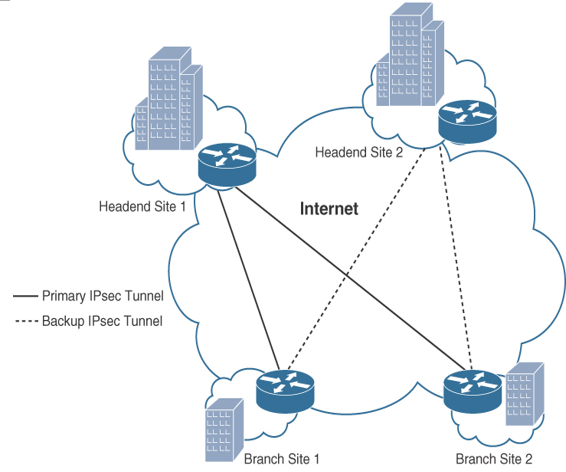
Figure 8-10 IPsec Direct Encapsulation Example
DMVPN
Dynamic Multipoint VPN (DMVPN) is a Cisco IOS solution for building IPsec over GRE VPNs in a dynamic and scalable manner.
DMVPN relies on two key technologies:
- Next Hop Resolution Protocol (NHRP): NHRP creates a mapping database for all spoke tunnels to real public addresses.
- Multipoint GRE (mGRE): mGRE is a single GRE interface that provides support for multiple GRE and IPsec tunnels to reduce the complexity and the size of the configuration.
DMVPN supports a reduced configuration framework and supports the following features:
- Hub router configuration reduction, with a single mGRE interface and a single IPsec profile to manage all spoke routers
- Automatic IPsec initiation and auto-creation of GRE tunnels without any IPsec peering configuration
- IP unicast, IP multicast, and dynamic routing protocol support without the need for a service provider
- Remote spoke routers with dynamic IP addressing
- Spoke routers behind dynamic Network Address Translation (NAT) and hub routers behind static NAT
- Dynamic spoke-to-spoke tunnels for partial scaling or fully meshed VPNs
- Support for all the GRE tunnel benefits, such as QoS, deterministic routing, and redundancy scenarios
Each remote site is connected using a P2P GRE tunnel interface to a single mGRE headend interface. The headend mGRE interface dynamically accepts new tunnel connections.
Redundancy can be achieved by configuring spokes to terminate to multiple headends at one or more hub locations. IPsec tunnel protection is typically used to map the cryptographic attributes to the tunnel that is originated by the remote peer.
Dead peer detection (DPD) can be used to detect the loss of a peer IPsec connection. NHRP is configured on both the headend and the spoke routers and is a requirement for using mGRE interfaces.
Figure 8-11 shows an example of a DMVPN network with two different DC hub locations along with two spoke locations that are using certificate authentication via a PKI infrastructure with a Microsoft CA.
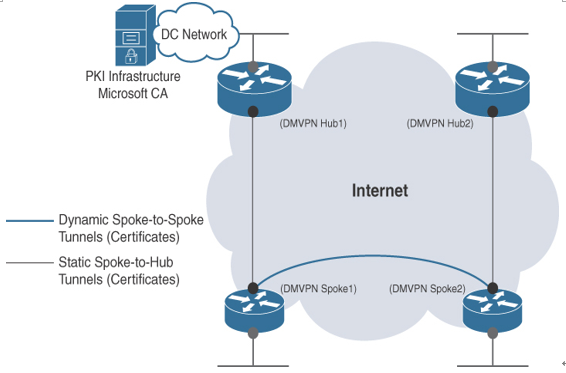
Figure 8-11 DMVPN Example




