Site-to-Site VPN Design – WAN for the Enterprise
3 min read
VPNs are typically deployed over some kind of shared or public infrastructure. VPNs are similar to tunnels in that they carry traffic over an existing IP infrastructure. VPN technologies use the Internet, Layer 3 MPLS WANs, and point-to-point connected IP infrastructures to transport data from end to end. A disadvantage of using VPNs over public networks is that the connectivity is best effort in nature, and troubleshooting is difficult because visibility is limited into the service provider’s infrastructure.
VPN Benefits
The major benefits of using VPNs are flexibility, cost, and scalability. VPNs are easy to set up and deploy over an existing infrastructure in most cases. VPNs enable network access to remote users, remote sites, and extranet business partners. VPNs lower the cost of ownership by reducing the WAN recurring monthly charges and standardizing VPN security policies. The geographic coverage of VPNs is nearly everywhere Internet access is available, which makes VPNs highly scalable. In addition, VPNs simplify WAN operations because they can be deployed in a secure and consistent manner.
Site-to-site VPN types include the following:
- Intranet VPNs: Site-to-site VPNs over the Internet offer an alternative WAN transport for interconnecting sites. Generally, the remote sites use their Internet connection to establish the VPN connection back to the corporate headend office. Site-to-site VPNs can also use an IP backbone provided by the service provider. The main use cases for site-to-site VPNs are primary WAN transport, lower-cost MPLS WAN backup, and connection to secure cloud services. Cisco ASA, Cisco ISR, and Cisco ASR Series routers are commonly used for site-to-site VPNs with IPsec over GRE to support the deployment of IGPs. Site-to-site VPNs also include cloud solutions for connectivity to AWS, Azure, and Google Cloud.
- Extranet VPNs: This is another form of site-to-site VPN infrastructure for business partner connectivity that also uses the Internet or a private infrastructure for network access. Keep in mind that it is important to have secure extranet network policies to restrict the business partners’ access. Typically, these types of VPNs terminate in a partner-designated firewalled DMZ.
Figure 8-9 shows VPN examples for home users, mobile users, and site-to-site VPNs.
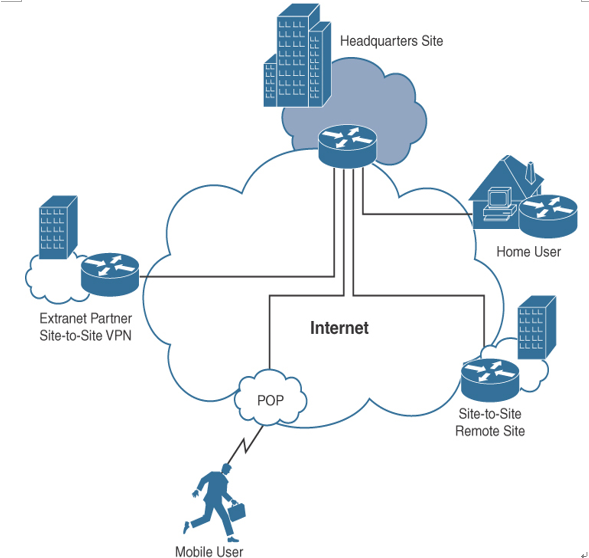
Figure 8-9 VPN Examples
IPsec
Internet Protocol Security (IPsec) is a network layer protocol suite for encrypting IP packets between two hosts and thereby creating a secure “tunnel.” The IETF defined IPsec in RFC 4301. IPsec uses open standards and provides secure communication between peers to ensure data confidentiality, integrity, and authenticity through network layer encryption. IPsec connections are commonly configured between firewalls, VPN appliances, or routers that have IPsec features enabled. IPsec can scale from small to very large networks.
The IPsec protocols include Internet Security Association and Key Management Protocol (ISAKMP) and two other IPsec IP protocols: Encapsulating Security Payload (ESP) and Authentication Header (AH). IPsec uses symmetrical encryption algorithms to provide data protection. These algorithms need a secure method to exchange keys to ensure that the data is protected. Internet Key Exchange (IKE) ISAKMP protocols provide these functions. There are two versions of IKE: IKEv1 and IKEv2. IKEv1 works in two modes: Main mode (with six messages) and Aggressive mode (which uses three messages). IKEv2 is an enhancement to IKEv1 and uses four messages. IKEv1 requires symmetric authentication, whereas IKEv2 uses asymmetric authentication. ESP is used to provide confidentiality, data origin authentication, connectionless integrity, and anti-replay services. AH is used to provide integrity and data origin authentication, usually referred to as just authentication.
IPsec can secure data from eavesdropping and modification using transform sets, which give you varying levels of strength for data protection. IPsec also has several hash message authentication codes (HMACs) available to provide protection from attacks such as man-in-the-middle, packet-replay, and data-integrity.




